Those of us working in Information Security and Risk Management have known for some time about the forthcoming Digital Operational Resilience Act (DORA) which implements the new cybersecurity directives for financial organisations and IT suppliers in the EU. While many firms already have strong Information Security policies, DORA challenges us to go further. The question isn’t whether we are compliant with current standards, but how we address DORA’s additional demands, particularly as the January 2025 deadline approaches.

While attending and speaking on a panel at the Operational Resilience, Outsourcing & 3rd Party Risk conference in London recently, it became clear that DORA is garnering a lot of attention and is a major focus, highlighting the need for considerable understanding of the legislation. Achieving compliance and securing 3rd party buy-in present significant challenges though, since 3rd parties must demonstrate a clear readiness and willingness to actively engage in the process.
The good news for those of us actively managing Information Security programmes is that we already meet many of DORA’s requirements. However, DORA introduces more stringent expectations in certain areas, potentially exposing gaps that need to be addressed. In this article, we show how the management team at Kurtosys examined these gaps and share how, over the past two years, we have proactively addressed them, leading to our full compliance ahead of the Act’s implementation deadline.
At Kurtosys, we have a long-standing commitment to implementing and adhering to best practices in Information Security. With over 12 years of ISO 27001 certification, complemented by a robust, internally developed framework we established several years prior to this, Kurtosys have built a strong foundation for operational resilience. The experience has made interpreting, understanding and aligning with DORA’s requirements a straightforward process. By examining DORA’s five key pillars, we have identified areas for enhancement and taken proactive steps to ensure full compliance.

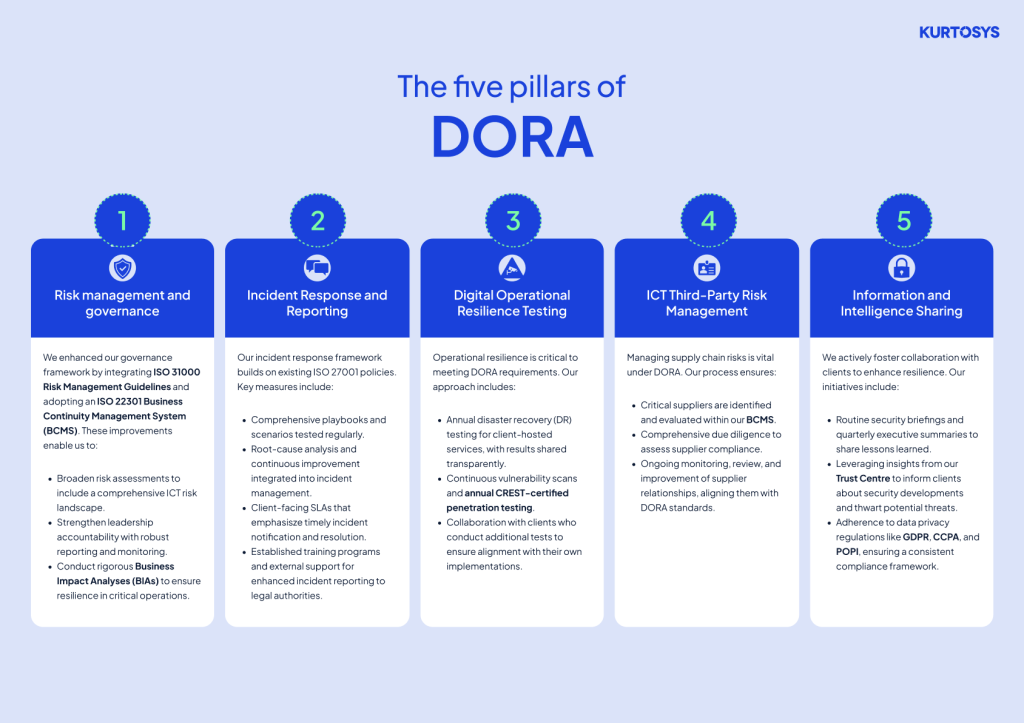
What have we done to adhere to DORA’s 5 key pillars?
Risk management and governance
DORA requires the responsibility of leadership within financial sector businesses to understand the ICT risk landscape and manage its ICT initiatives and outsourcing. Whilst we already had well defined leadership responsibilities and risk assessments within our ISO 27001 Information Security Management System, we made some significant improvements to this by adopting a comprehensive ISO Integrated Management System which then allowed us to widen our Risk Management initiatives using ISO 31000 Risk Management Guidelines. Additionally, we implemented and certified an ISO 22301 Business Continuity Management System to improve maturity and ensure that our Business Impact Analysis (BIA) was sufficiently robust.Incident response and reporting
Our ISO 27001 Information Security Management System and certification encompasses comprehensive policies and procedures for managing both operational and security incidents. Our incident response plans include contingencies and playbooks for multiple scenarios which are regularly tested to ensure effectiveness. We have incident reporting procedures that specify notification and escalation protocols, provide analysis and root cause identification, as well as linking continuous improvement processes. We maintain SLAs with clients that outline incident reporting and remediation commitments. This is all underpinned with established training programs, experienced supervision, external support where appropriate and registrations to support reporting to legal authorities.Digital operational resilience testing
The introduction of ISO 22301 Business Continuity certification has enhanced our operational resilience processes, particularly by strengthening our Business Impact Analysis (BIA) and supply chain management. In accordance with existing practices, we perform an annual disaster recovery (DR) test on Client Hosting Services and report the results to external stakeholders. Complementing this, our existing ISO 27001 Information Security certification defines robust policies and procedures for vulnerability and patch management. We conduct continuous vulnerability scanning and annual independent penetration testing by a CREST certified test company, with results reported to our clients. We conduct our tests across our platform, or areas requiring additional scrutiny, and some clients opt to conduct their own tests on their implementations – a process we actively support. Additionally, we maintain Internal monitoring of employee accounts and devices with testing and security awareness also applies.ICT third-party risk management
Both ISO 27001 and ISO 22301 programs include policies and procedures which have strengthened our supplier risk and 3rd party service management processes. Critical suppliers are identified and included in our Business Impact Analysis (BIA) and due diligence identifies other parties in any of our supply chains partners. Our procedures cover assessing, implementing, operating, monitoring, reviewing, maintaining and improving supplier relationships.Information and intelligence sharing
Within our policy documentation, we identify appropriate legislation impacting our business and which we need to align and comply with such as the Data Privacy laws: GDPR, CCPA and POPI. Our Risk, Security and Compliance team actively collaborate with our clients to share insights and learn lessons from data we collect. This approach has successfully thwarted potential security breaches and mitigated actions of threat actors. Clients are encouraged to engage in routine security briefings to discuss these topics, and we provide summaries as part of our quarterly executive briefings.
In conclusion, what we have learnt is that the major gaps in a typical ISO 27001 implementation fall into four main categories:
- Business continuity
- Security testing
- Supply chain risk management
- Incident reporting
To address these gaps, we have supplemented our ISO 27001 implementation with additional policy by adopting ISO 31000 and 22301. Along with some critical updates to our existing policies, this approach has enabled us to implement straightforward initiatives that improve and enhance our processes and ensure compliance with DORA requirements.

Since we started on these DORA initiatives, we have also created a Trust Centre which houses comprehensive documentation and searchable content to support these efforts. We encourage both clients and prospects to subscribe and use the Trust Centre, as it is consistently updated and provides notifications when new information or changes are available. Additionally, we can track what content is being accessed and engage interactively to speed up the Due Diligence process. Notably, one of the most popular downloads from our Trust Centre is the ISO 22301 Business Continuity certificate which highlights the current emphasis on DORA compliance.


Finally, when it comes to putting all the pieces together, we have also developed an addendum to our standard terms that ensures the regulatory requirements of DORA are reflected in our existing client contractual obligations. This ensures that our existing client contractual obligations reflect the necessary controls needed for our ICT services and supply chain management, bringing any existing or missing controls in line with DORA.